Hackers supporting Iran’s Islamic Revolutionary Guard Corps targeted scholars at a London university and Middle East journalists by posing as British academics, a cybersecurity firm has said.
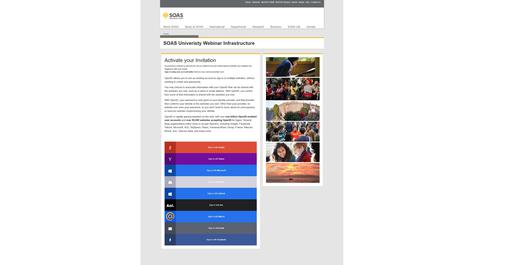
Earlier this week, Proofpoint exposed a scheme by Iranian threat actors TA453 – also known as Charming Kitten, APT35 Ajax and Phosphorus. The group, it said, targeted scholars at the University of London’s School of Oriental and African Studies (SOAS) by sending them emails from Gmail accounts in which they posed as fellow scholars.
In what Proofpoint dubbed “Operation SpoofedScholar”, from at least January 2021 the group struck up conversations with academics and reporters via email before sending them a registration link for an online conference that required the user’s sign-in credentials, as a means of accessing their usernames and passwords.
One targeted individual received was contacted by someone purporting to be a “senior teaching and research fellow at SOAS University in London”, who later sent them a detailed invitation to a conference entitled “The US Security Challenges to the Middle East”.
The sign-up link took them to a real page that had been compromised by the group, SOAS Radio, where they were asked to enter their login details. The attack was one of the most ambitious yet as the hacking group exchanged frequent emails with targets to gain their trust, and even offered to have phone calls and video chats with them about the fake conference. The willingness to chat in real-time was unique to this attack.
Along with targeting SOAS scholars, TA453 targeted a small number of other organizations, including professors and think-tanks focusing on the Middle East. The small number of targets suggested a highly focused strategy from the bad actors.
Though the reason for these specific targets is unknown, Proofpoint’s experts speculate that it pinpointed individuals who might have information on Iranian dissidents living in exile, and/or on Iran’s nuclear program.
In a statement, SOAS said no personal information was obtained by the group and its own internal data systems were not affected. It also strove to point out that SOAS Radio was not part of the official stable of SOAS academic domains.
"Once we became aware of the dummy site earlier this year,” a spokesperson said, “we immediately remedied and reported the breach in the normal way. We have reviewed how this took place and taken steps to further improve protection of these sort of peripheral systems.”
Proofpoint could not confirm whether the IRGC was behind the campaign. But the tactics, techniques and the nature of the targeting gave the firm "high confidence" that it was involved. The IRGC, specifically the IRGC Intelligence Organization, collects intelligence and conducts operations in support of a variety of assigned responsibilities," the firm explained.
"According to the Meir Amit Intelligence and Terrorism Information Center’s November 2020 report, some of the IRGC IO’s responsibilities include foiling political subversion, combating western cultural penetration, and supporting the arrest of Iranian dual nationals."
It also warned that while it has worked with the authorities to notify victims, the group might well continue to try to masquerade as academics again in future.
Related coverage:
Iranian Government Hackers Target Religious and Ethnic Minorities
US Seizes Almost 100 Domain Names Used by the Revolutionary Guards
Iran Named as Top Cyber Security Risk to Canada
Coercion by a Thousand Proxies: How Iran Targets Dissidents in Sweden

























comments