
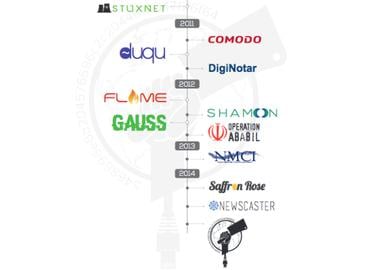
Cyber attacks are big news, especially when governments are involved. In recent years, evidence has emerged that Iranian attackers have orchestrated a range of attacks on the United States, Europe and numerous other countries around the world.
The latest report is by US security firm Cylance published on December 2. It states that an Iran-backed hacking campaign, now dubbed “Operation Cleaver,” accessed the computer networks of 16 countries around the world, affecting airports, hospitals, governments and more.
Given that the Iranian government began heavily investing in its cyber capabilities after the Stuxnet computer virus hit its nuclear program in 2010 – a joint US-Israeli project that reportedly destroyed about a fifth of Iran’s nuclear centrifuges by causing them to spin out of control — the report’s claims are not implausible.
IranWire spoke to Ali Bangi, the director of ASL19, a research and technology lab that supports Iranians wanting to bypass internet censorship, to determine whether he thought this latest information was trustworthy and to gain some insight into Iran’s cyber capabilities.
Read yesterday’s interview with Collin Anderson, an expert on internet censorship in Iran, to learn more on the story.
1. Is Cylance a reliable internet security outlet or could this be a form of US propaganda designed to come out shortly after nuclear talks came to a "standstill"?
I don't know if the report is propaganda, related to the nuclear talks. However, the report begins with quotes from high-ranking US military and intelligence personnel, as well as Gabi Siboni from Israel's Institute for National Security Studies. These quotes are about Iran's cyber capabilities (alongside China and Russia) as an adversary to US and Israel. Cylance’s choice to highlight Iran's cyber capabilities seems one-sided and biased, and diminishes their credibility to conduct this research objectively. Israel and the US have launched cyber attacks against Iran, including Stuxnet, which was designed to use electronic means to impact our physical world, a very real and unprecedented threat. The report seems to be a warning that Iran has gained the same cyber capabilities as the US and Israel, and Iran is retaliating by launching physical attacks around the world through cyberspace.
2. Is Iran capable of committing the cyber attacks the Cylance report says it has?
Iran has gained sophisticated cyber capabilities after Stuxnet and Flame. However, the US and Israeli military and intelligence community seems to have exaggerated these capabilities. They have accused the Iranian government — not just hackers — of launching many cyber attacks, but have not been able to produce solid evidence. Many of the capabilities noted in the Cylance report were mentioned in former reports, including Fire Eye's Operation Saffron Rose investigation, which came out last year. Fire Eye's investigation did a good job of documenting the capabilities of Iranian hackers and the evolution of their attacks post-Stuxnet. However, the report did not make a direct connection between the Iranian government and the hackers.
3. How can Cylance guarantee the hackers are Iran-backed?
Given the nature of cyber attacks, it is difficult to "guarantee" who is behind them. Unless the perpetrators take responsibility for them, such as the Stuxnet case, where US officials have taken responsibility for launching the attacks in collaboration with Israel. While I do not undermine Iran's cyber capabilities, I do not find Cylance’s evidence compelling that the Iranian government was indeed behind this attack. For example, the use of "Persian hacker names" is weak evidence that the Iranian government bears responsibility for the attacks.
4. Are authoritarian regimes increasingly using cyber attacks on other states and companies?
Cyber attacks have been launched by both authoritarian and democratic states. Both democracies and dictatorships have demonstrated their cyber “arsenal” and their ability to attack and assert their power online. At ASL19, we have reported on the Iranian government's efforts to control information online in the lead up to the last presidential election as a form of “just-in-time" censorship. Edward Snowden's revelations have also shown how pervasive US government surveillance has been, both in the US and globally. As such, cyber attacks and information controls online are practiced by both authoritarian regimes and democracies. Overall, it seems that state-sponsored cyber attacks are on the rise.
visit the accountability section
In this section of Iran Wire, you can contact the officials and launch your campaign for various problems





















comments
Question one: Who started the cyber attack first? Israel- USA- Iran? Your answer may lie on Iran's nuclear facilities some years ago. Dummies drink the night before, make some rules the day after and call it policy, consequences unknown.
Question two: A house with solid foundation would go down or a house with solid structures and walls? Your answer may lie within the history of the regions in the world such as China and Middle- East. Sanctions over sanctions on Iran may make the life hard but it will never cripple its foundations.
Question three: 18 trillion debt or zero debt? Your answer may lie on real economy "not" phony economy that some drinkers above claim to have. China economy just surpassed US phony economy according to IMF.
Question four: Your turn. ... read more